Cybercriminals leveraging pandemic news to attack banks and financial services in SEA, says Kaspersky
We may be in the middle of a pandemic but according to Kaspersky, cybersecurity professionals can’t seem to catch a break as the usual suspects are taking advantage of the situation to target banking and financial services in Southeast Asia.
“It is becoming clear that these threat actors will keep on using topics related with the pandemic to trick the human mind. While vaccines are here, the situation continues to be uncertain. Countries are still implementing lockdowns, virtual learning and working are both here to stay, and digital payments are on the rise. This means IT infrastructure remains outstretched, further opening loopholes for threats targeting beyond Windows and internet-facing network devices as well as multi-platform and supply chain attacks,” reveals Park, Senior Security Researcher, Global Research and Analysis Team (GReAT) at Kaspersky.
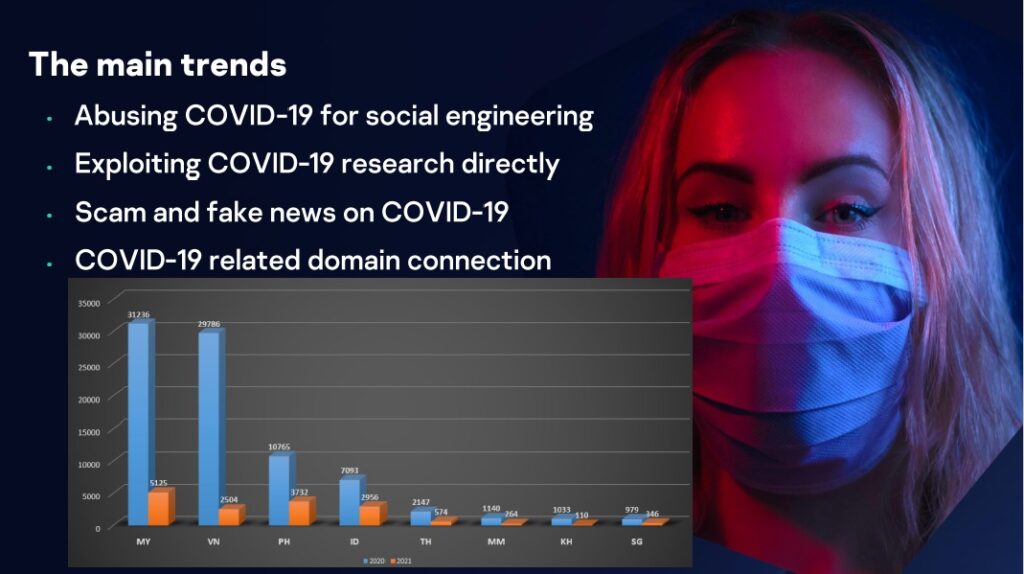
According to Park, more than 80,000 COVID-related domain connections and malicious websites were detected in Southeast Asia along with Malaysia registering the highest number followed by Vietnam, the Philippines and Indonesia. This trend is expected to continue until 2021 even as vaccine programmes roll out in various stages in the region.
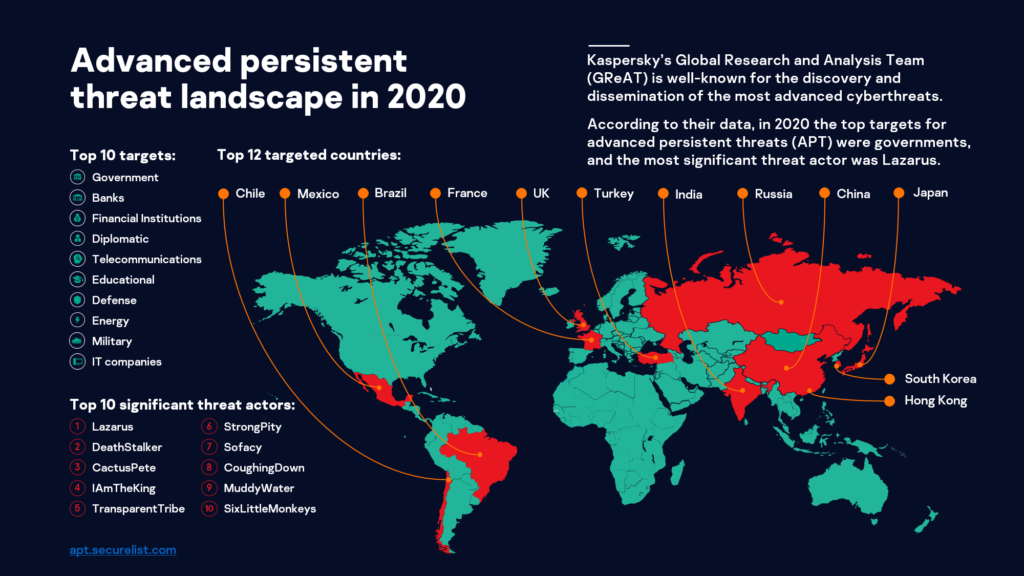
Further, Kaspersky’s GReAT shared that banks and financial institutions were the second and third most targeted sectors in 2020. One particularly pernicious malware in SEA is JsOutProx that exploit file names associated with bank-related businesses and use heavily obfuscated script files, an anti-evasion tactic. This social engineering technique particularly preys on bank employees to get inside the institution’s network.
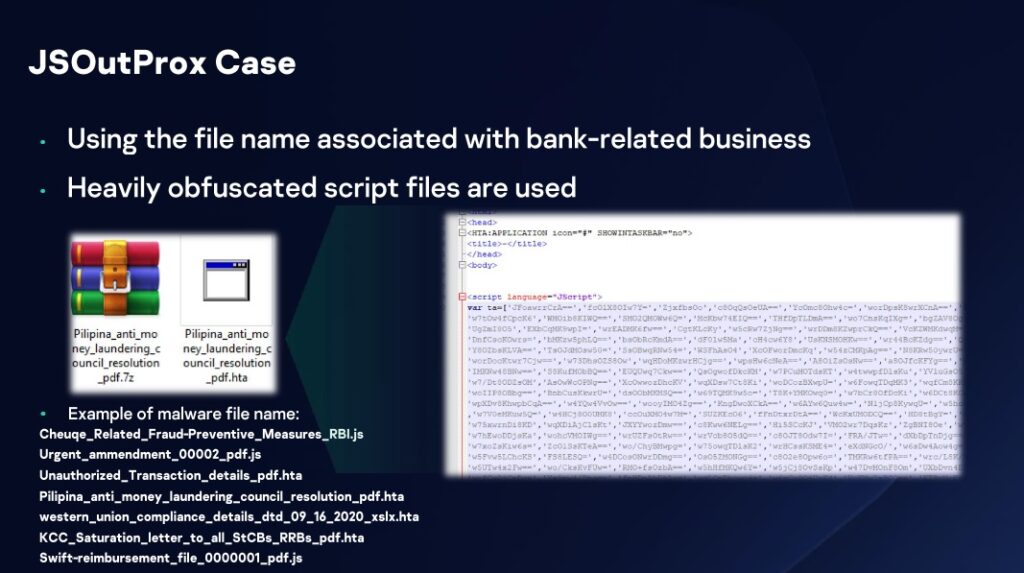
Once in, Park shares that “JSOutProx can load more plugins to perform malicious acts against its victims including remote access, data exfiltration, command and control (C2) server takeover, and more.”
Cybercriminals are also angling for the growing cryptocurrency business in SEA with a confirmation that the infamous Lazarus group has compromised one cryptocurrency outfit in Singapore.

Mr. Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky
In terms of the factors behind the increased threats against the sector, Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky comments, “Cryptocurrency is steadily being embraced in SEA, hence it is a natural progression for cybercriminals to set their eyes here. Its growth is part and parcel of the region’s digital transformation, and is parallel to the increased adoption of e-commerce and digital payments.”
“As we continue to move our money to the online world, we have also witnessed massive data breaches and ransomware attacks last year which should serve as a warning for financial institutions and payment service providers. It is crucial for banking and financial services providers to realise, as early as now, the value of intelligence-based, proactive defense to fend off these costly cyberattacks,” Yeo adds.
“We have been monitoring Kimsuky’s strong presence in South Korea. Our research showed they are using two infiltration techniques — attacks via spearphishing and attacks against supply chain. Either way, they target cryptocurrency investors to exfiltrate data and for remote access. With the group showing strong financial motivation, it is highly possible that their attacks can go beyond South Korea, particularly towards its neighbouring regions like Southeast Asia,” explains Park.
To improve banks’ and financial organisations’ cyber defences, experts in Kaspersky suggest the following:
- Integrate Threat Intelligence into your SIEM and security controls in order to access the most relevant and up-to-date threat data
- Conduct regular security training sessions for staff, ideally a personalised one like Kaspersky Adaptive Online Training (KAOT) which uses a cognitive-driven approach, taking into account the abilities and needs of each and every learner
- Use traffic monitoring software – like Kaspersky Anti Targeted Attack Platform (KATA)
- Install the latest updates and patches for all of the software you use
- Forbid the installation of programs from unknown sources
- Perform regular security audit of an organization’s IT infrastructure
- For endpoint level detection, investigation and timely remediation of incidents, implement EDR solutions such as Kaspersky Endpoint Detection and Response which can catch even unknown banking malware